
SWIFT CSP 2026: Changes You Need to Know
What’s New in the SWIFT CSP 2026: Strengthening Cybersecurity for a Connected Financial World
The SWIFT Customer Security Controls Framework (CSCF) continues to evolve alongside the rapidly changing cyber threat landscape. With the release of the SWIFT CSP 2026 version (CSCF v.2026), SWIFT is reinforcing its commitment to industry-wide resilience, tighter security integration, and proactive risk management for all network participants.
While the core structure of the framework remains stable, v2026 introduces several significant updates over the 2025 SWIFT CSCF framework — notably new mandatory requirements, expanded component coverage, and clarified expectations for cloud and API-based environments. Here’s a breakdown of the most important changes financial institutions need to know.
 1. Back Office Data Flow Security Is Now Mandatory
1. Back Office Data Flow Security Is Now Mandatory
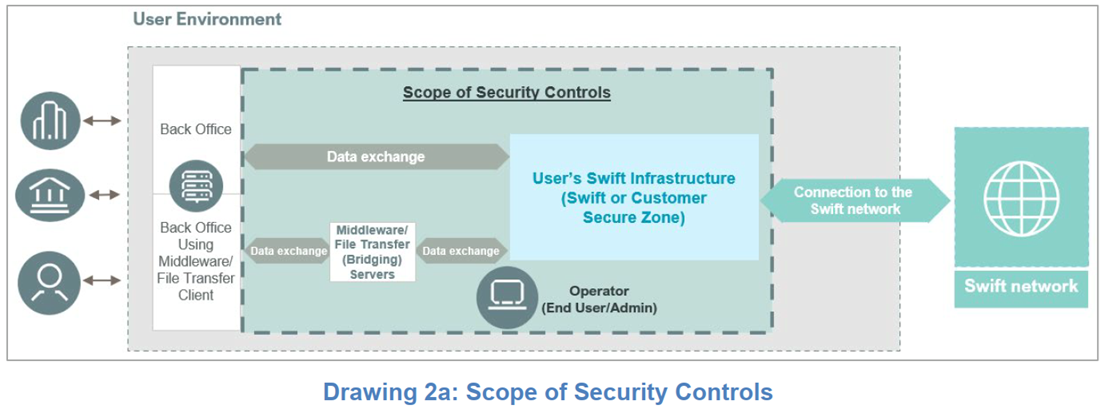
Perhaps the most impactful change is that Control 2.4 – Back Office Data Flow Security has moved from advisory to mandatory status.
This control focuses on securing the data exchanges between a user’s secure zone and back-office systems, particularly when the data isn’t protected end-to-end.
In 2026, institutions must ensure:
-
- Protection of bridging servers that manage communication between secure zones and back-office environments.
-
- Security of direct flows between these systems when modern, end-to-end protection isn’t in place.
SWIFT has also outlined a phased roadmap toward 2028, when all remaining legacy data flows will be brought under full compliance.
Takeaway: Start validating your data transfer architecture now—especially middleware and file transfer layers—to ensure readiness for full enforcement.
 2. Customer Client Connectors Now In-Scope for Multiple Controls
2. Customer Client Connectors Now In-Scope for Multiple Controls
The concept of “customer client connectors”—such as file transfer clients, middleware, or API endpoints—has been expanded.
Previously advisory, these components are now mandatory in-scope for numerous key controls, including:
-
- 1.2 Operating System Privileged Account Control
-
- 1.3 Virtualisation/Cloud Platform Protection
-
- 1.4 Restriction of Internet Access
-
- 2.2 Security Updates
-
- 2.6 Operator Session Confidentiality and Integrity
-
- 6.1 Malware Protection
-
- 6.4 Logging and Monitoring
This aligns all user endpoints—both servers and clients—under a single, standardized security expectation.
Impact: Organizations that previously self-classified as Architecture Type B (no Swift footprint) may now need to attest under Type A4, which includes customer connectors.
 3. Alliance Connect Evolves to Software-Defined Networking
3. Alliance Connect Evolves to Software-Defined Networking
Between 2026 and 2028, SWIFT will transition its Alliance Connect portfolio to Software-Defined Wide Area Network (SD-WAN) technology.
A major innovation is the introduction of the Alliance Connect Virtual on Premises VPN, a virtual VPN solution deployed on the customer’s own virtual machine.
This new VPN model is explicitly in scope for multiple CSCF controls, ensuring that institutions adopting it maintain equivalent levels of security as with traditional hardware (SRX) or cloud-hosted VPNs (vSRX).
Why this matters: The move reflects SWIFT’s long-term shift toward virtualized and cloud-compatible connectivity models, aligning with broader industry modernization trends.
 4. Control Clarifications and Enhancements
4. Control Clarifications and Enhancements
The 2026 update refines several existing controls, improving clarity and implementation consistency:
-
- Containerization (Control 1.3): Containers are now treated as co-hosted by default, but isolation is acceptable if supported by a risk assessment.
-
- Cryptography Guidance: The Knowledge Base article 5021566 has been refreshed to align with SWIFT’s post-quantum cryptography strategy.
-
- System Hardening (2.3): Now explicitly includes Windows Management Instrumentation (WMI) and PowerShell.
-
- Multi-Factor Authentication (4.2): MFA is now required for external privileged firewall access and for Alliance Security Officer (LSO/RSO) accounts.
-
- Malware Protection (6.1): Expands coverage to include non-Windows systems in secure zones.
-
- Security Awareness (7.2): Updated to reference AI-related threats, including Deepfakes.
-
- Penetration Testing (7.3A): Updated with new community-driven guidance.
Bottom line: v2026 focuses less on new controls and more on improving the precision, consistency, and modern relevance of existing ones.
 5. Updated Scope and Terminology
5. Updated Scope and Terminology
Several definitions and scope boundaries have been updated to reflect evolving technologies and deployment models:
-
- Clarifications around bridging servers, back-office first hops, and customer connectors.
-
- Expanded definitions for service providers (now includes third parties, Swift connectivity providers, and Group Hubs).
-
- General IT environment now explicitly includes servers supporting change and release management processes.
-
- Visual updates to diagrams in Appendices B and G better represent hybrid and API-based architectures.
In short: SWIFT is making the framework more reflective of modern financial infrastructures—where cloud, APIs, and shared services play a central role.
 6. AI Tools and Risk Management
6. AI Tools and Risk Management
While SWIFT hasn’t issued specific requirements around AI-based tools, v2026 formally recognizes AI-related risks.
Institutions using AI for compliance, monitoring, or operational purposes must apply the same standards of confidentiality, integrity, and availability as for traditional systems. We expect AI to become an essential part of compliance and security over the next few years, and we encourage our clients to get a head start in understanding their security posture.
 7. End-of-Life and Planning Ahead
7. End-of-Life and Planning Ahead
SWIFT confirms that Alliance Access Integration Platform (IPLA) and Swift Integration Layer (SIL) will reach end-of-life in 2026, though they remain in-scope until then.
Appendix G now includes new visuals showing shared responsibility models for cloud environments, aligning CSCF with common IaaS and SaaS governance practices.
 Final Thoughts: Preparing for SWIFT CSP 2026 Compliance
Final Thoughts: Preparing for SWIFT CSP 2026 Compliance
The 2026 release isn’t a revolutionary overhaul—but it’s a critical step forward in harmonizing security expectations across all types of Swift participants, especially as organizations adopt cloud services and API integrations.
World Informatix Cyber Security Inc. is a global leader in helping financial institutions navigate the SWIFT attestation requirements
For compliance teams, the top priorities for the coming year should be:
-
- Implementing Control 2.4 (Back Office Data Flow Security) in full.
-
- Reassessing architecture classification if customer connectors are used.
-
- Updating MFA, endpoint, and logging policies to reflect the new scope.
-
- Preparing for future SD-WAN and VPN transitions under the Alliance Connect modernization.
By proactively adapting now, financial institutions will not only meet their 2026 attestation obligations but also enhance operational resilience against tomorrow’s cyber threats.

About World Informatix Cyber Security
World Informatix Cyber Security (WICS) has helped financial institutions of all sizes – from small regional banks to Central Banks and the United Nations, navigate the SWIFT Customer Security Programme since 2016.
As one of the original CSP assessors and the lead incident response from the largest SWIFT attack at the Central Bank of Bangladesh in 2016, our experience provides a comprehensive and holistic approach to security the SWIFT payment system.




