
Unveiling SWIFT CSP 2025 Findings: Key Weaknesses and Security Insights
Even after nearly a decade of SWIFT CSP enforcement, one truth remains – compliance is not security. Every year, attackers evolve faster than institutions can patch, harden, or audit. Our analysis of SWIFT CSP 2025 Findings reveal where the cracks still form, and how to close them.”
As one of the original SWIFT CSP assessors, World Informatix Cyber Security (WICS) has been conducting detailed SWIFT CSP assessments since 2016 for a wide range of financial organizations across regions. These engagements have given us a data-rich view of how financial environments are evolving, and where recurring weaknesses continue to appear in implementing SWIFT’s Customer Security Controls Framework (CSCF).
From our cumulative analysis of recent assessments, we’ve identified control areas that still present challenges for many institutions, especially in maintaining strong, auditable evidence of compliance and ensuring operational resilience across SWIFT zones.
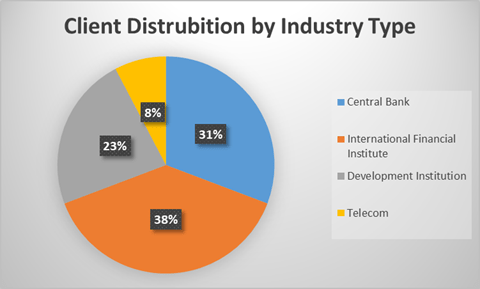
Who We’ve Assessed: A Snapshot of Our 2025 Client Landscape
Our 2025 assessments covered a diverse mix of financial institutions — including central banks, commercial banks, regional banks, microfinance institutions, International financial institutions and payment processors. Each client faces unique challenges in balancing compliance and operational efficiency, and our comparative data offers valuable insights into these varying risk postures.
The Data Speaks: Analysis from SWIFT CSP 2025 Findings
When we aggregate findings across clients, the data shows recurring weak spots in both technical and procedural controls.
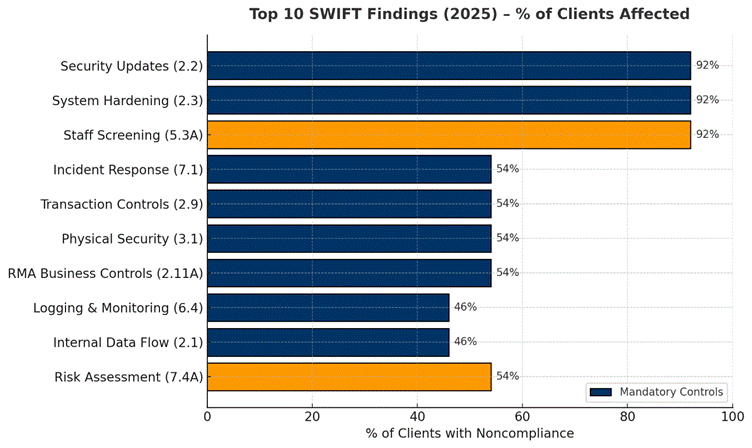
The chart below highlights the Top 10 SWIFT Findings, ranked by total count and percentage of customers affected, offering a clear view of where institutions must pay attention.
Key Findings from WICS 2025 CSP Assessments
Our 2025 assessment cycle revealed that while control implementation across SWIFT environments continues to mature, several recurring weaknesses remain — particularly in areas requiring ongoing operational discipline rather than one-time compliance actions. When grouped by SWIFT’s seven security principles, Principle 2: Protect the Environment and Principle 5: Detect and Respond account for more than two-thirds of total noncompliance. This indicates that while governance and policy-level controls are largely in place, operational execution and evidence maturity remain the bottlenecks.
1. Patch and Configuration Management Gaps (92% of Clients)
The most persistent weaknesses in 2025 were delayed security updates and inconsistent system hardening — both mandatory controls (2.2 and 2.3).
Even though most institutions maintain enterprise patch management programs, these often overlook SWIFT-specific components such as messaging interfaces, middleware servers, or jump hosts. Hardening checklists were frequently outdated or diverged from SWIFT and CIS benchmarks following system upgrades.
Risk: Unpatched or misconfigured systems remain one of the most direct routes for compromise, giving attackers footholds in critical SWIFT zones.
2. Human and Insider Risk Management (92% of Clients)
Despite technology investments, staff screening and role validation remain one of the most neglected areas. Advisory Control 5.3A was found deficient at nearly every institution assessed.
Screening was often limited to pre-employment checks, leaving out contractors, consultants, and periodic re-screening for financially sensitive roles. Periodic checks for precursor indicators such as criminal proceedings, conflict of interest and financial credit verification are often not conducted periodically to evaluate ongoing changes to insider threats.
Risk: Inadequate vetting increases the potential for insider fraud, collusion, or unauthorized access — risks that no firewall can mitigate.
3. Incident Response and Detection Weaknesses (54% of Clients)
Roughly half of the institutions lacked SWIFT-specific incident response playbooks, escalation matrices, or integration with enterprise SOC workflows.
While many organizations have a general IR plan, few have tested or simulated SWIFT payment fraud scenarios — a critical gap when rapid discovery & containment and fund recovery are time-sensitive.
Complementing this, logging and monitoring (Control 6.4) continues to lag, with limited 24×7 coverage and incomplete log collection from SWIFT secure zones.
Risk: Without a tested SWIFT response plan or targeted monitoring, organizations risk delayed detection and prolonged recovery in case of a breach by which time fraudulently transacted funds have moved out of jurisdiction and changed hands.
4. Transactional and Access Control Weaknesses (54% of Clients)
Controls governing transaction business hours, transaction limits, RMA relationships, and physical security remain inconsistent.
Many institutions still SWIFT and other payment systems open during off-hours or weekends without additional safeguards — a known vulnerability window exploited in prior SWIFT-related fraud cases.
Old/unused or dormant RMA counterparty relationships also persist which increase the likelihood of being abused by attackers. Many RMA records do not include message-type restrictions, increasing exposure to fraudulent or misdirected transfers.
Risk: Weak business controls and unmaintained counterparties create exploitable paths for fraudulent payment initiation or manipulation.
5. Back-office Data Flow and Encryption Gaps (46% of Clients)
Roughly half of the organizations showed unclear internal back-office data flows between SWIFT interfaces and back-office systems. Encryption validation and configuration hardening were inconsistently implemented.
Risk: Attackers could intercept, alter, or monitor unencrypted message traffic within the secure zone, compromising transaction integrity.
6. Testing and Scenario-Based Risk Assessment (54% of Clients)
Advisory Control 7.4A revealed that most risk assessments remain generic penetration tests, not realistic SWIFT simulations. Few organizations validate whether defensive controls activate during a SWIFT-targeted attack.
Risk: Without real-world testing, institutions underestimate risk exposure and fail to detect gaps in control effectiveness until after an incident.
WICS Value-Added Approach to SWIFT Security
The 2025 assessments make one message clear: while most institutions have made significant progress in deploying SWIFT controls, many still struggle to prove that those controls work as intended. Patching delays, configuration drift, incomplete monitoring, and insufficient incident playbooks continue to create blind spots that can undermine even well-designed environments. The key challenge ahead is not compliance — it’s control assurance.
At World Informatix Cyber Security (WICS), we help institutions move beyond checkbox compliance to achieve measurable, sustainable security.
Our proprietary SWIFT assessment framework, aligned with SWIFT’s 3 core objectives, 7 principles, and 32 controls, evaluates over 200 control points to assess both compliance and operational effectiveness. This evidence-based approach provides a real-world view of how secure, monitored, and audit-ready your SWIFT environment truly is.
Because WICS has served as an investigating partner in high-impact cyber incidents, our consultants bring field-tested insight that transforms technical findings into actionable resilience. We don’t just identify gaps — we show clients how to close them with process, technology, and governance improvements that withstand real-world attacks.
How WICS Supports You in 2025
As organizations finalize their 2025 attestations, WICS continues to assist clients through:
- Pre-attestation readiness checks to validate documentation and control evidence
- Evidence-based gap analysis to confirm operational maturity
- Advisory alignment with the SWIFT CSP 2025 Framework, ensuring lasting compliance and resilience
In an environment where cyber threats evolve faster than annual attestations, success depends on demonstrating not only that controls exist — but that they are effective, tested, and sustainable.
WICS helps financial institutions turn compliance into confidence — building SWIFT ecosystems that are secure by design, resilient in practice, and ready for any audit.
Explore Similar Topics
- What Happens If You Don’t Meet Your SWIFT CSP Deadline?

- Unveiling SWIFT CSP 2025 Findings: Key Weaknesses and Security Insights

- SWIFT CSP 2026: Changes You Need to Know

- SWIFT CSP 2025: What Financial Institutions Must Know

- Understanding the 2025 SWIFT CSP Framework: Stabilization and Strategic Evolution


About World Informatix Cyber Security
World Informatix Cyber Security (WICS) has helped financial institutions of all sizes – from small regional banks to Central Banks and the United Nations, navigate the SWIFT Customer Security Programme since 2016.
As one of the original CSP assessors and the lead incident response from the largest SWIFT attack at the Central Bank of Bangladesh in 2016, our experience provides a comprehensive and holistic approach to security the SWIFT payment system.




